Connecting to Non-HyperPath Devices
Overview
HyperPath networks can connect integrate with non-HyperPath network devices via the External Routes feature. This feature allows you to access IoT devices, servers, and other network equipment that don't or can't have HyperPath installed from any HyperPath node
External Routes Configuration
To make non-HyperPath devices accessible through your HyperNet:
- Identify the HyperPath node that has direct connectivity to the non-HyperPath devices
- Access the token settings for this node
- Locate the
External Routesparameter - Specify the IP addresses or subnet ranges that should be reachable via this node. The configuration accepts individual IP addresses (e.g.,
192.168.1.10) or entire subnet ranges using CIDR notation (e.g.,192.168.1.0/24). - Save your settings
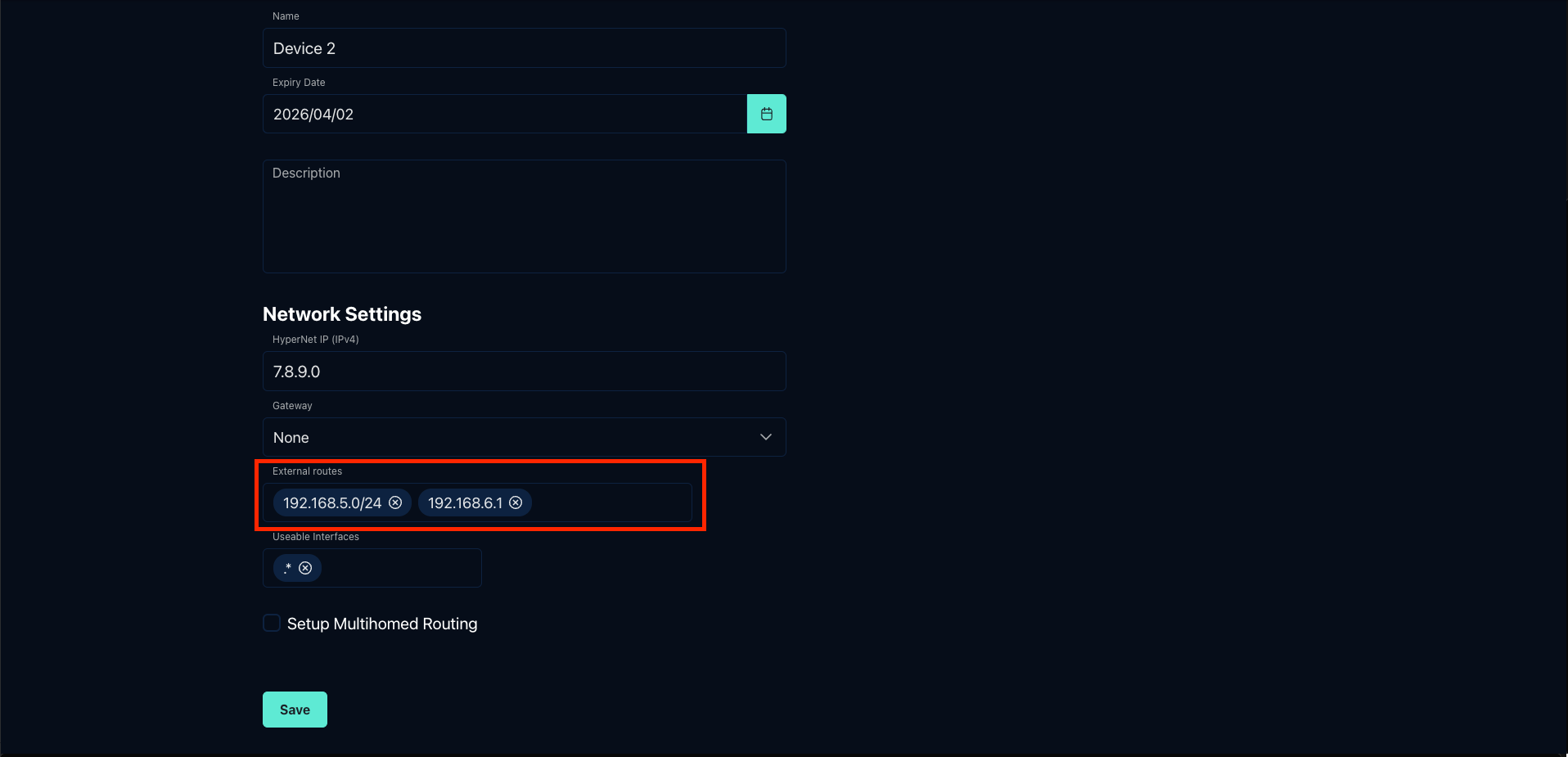
Once configured, other HyperPath nodes in your network will automatically route traffic destined for these external devices through the node with the specified External Routes.
IP Masquerading Requirements
For successful communication between HyperPath nodes and external devices, Network Address Translation (NAT) using IP Masquerading (MASQUERADE) must typically be enabled on the node with External Routes configured.
IP Masquerading performs several critical functions:
- Translates the source IP addresses of packets from remote HyperPath nodes
- Makes packets appear as if they originated from the local node with direct connectivity
- Enables external devices to respond correctly, as they'll send responses back to the local node
- Allows the local node to forward the responses back to the original HyperPath node
Setting Up IP Masquerading
On most Linux systems, IP Masquerading is configured using iptables:
iptables -t nat -A POSTROUTING -o <OUTGOING_INTERFACE> -j MASQUERADE
Replace <OUTGOING_INTERFACE> with the name of the network interface on the gateway that connects to the internet (e.g., eth0, wlan0). OpenWRT Configuration
On OpenWRT systems, HyperPath automatically adds the necessary MASQUERADE rule to the firewall when it runs. You can verify the current firewall rules by executing:
iptables -t nat -L -n -v
This will display all Network Address Translation (NAT) rules currently active in the firewall.
Troubleshooting
If you're experiencing issues connecting to non-HyperPath devices:
- Verify that the External Routes configuration includes the correct IP addresses/ranges
- Confirm that IP Masquerading is properly enabled on the node with External Routes
- Check that traffic forwarding is enabled on the system (
sysctl net.ipv4.ip_forwardshould be set to 1) - Ensure there are no firewall rules blocking traffic between the HyperPath node and external devices